Identity Providers
Notice
In order to manage your identity-providers, stations, ... you need to get an organization. Please contact us, such we can provide you a realm in which you can manage all your stations, users and identity providers. For more details on realms click here.
Identity providers allow for an alternative way to login into a realm. They are set up by the administrator with external third-party OIDC providers such as google, Keycloak, and many others.
Setup
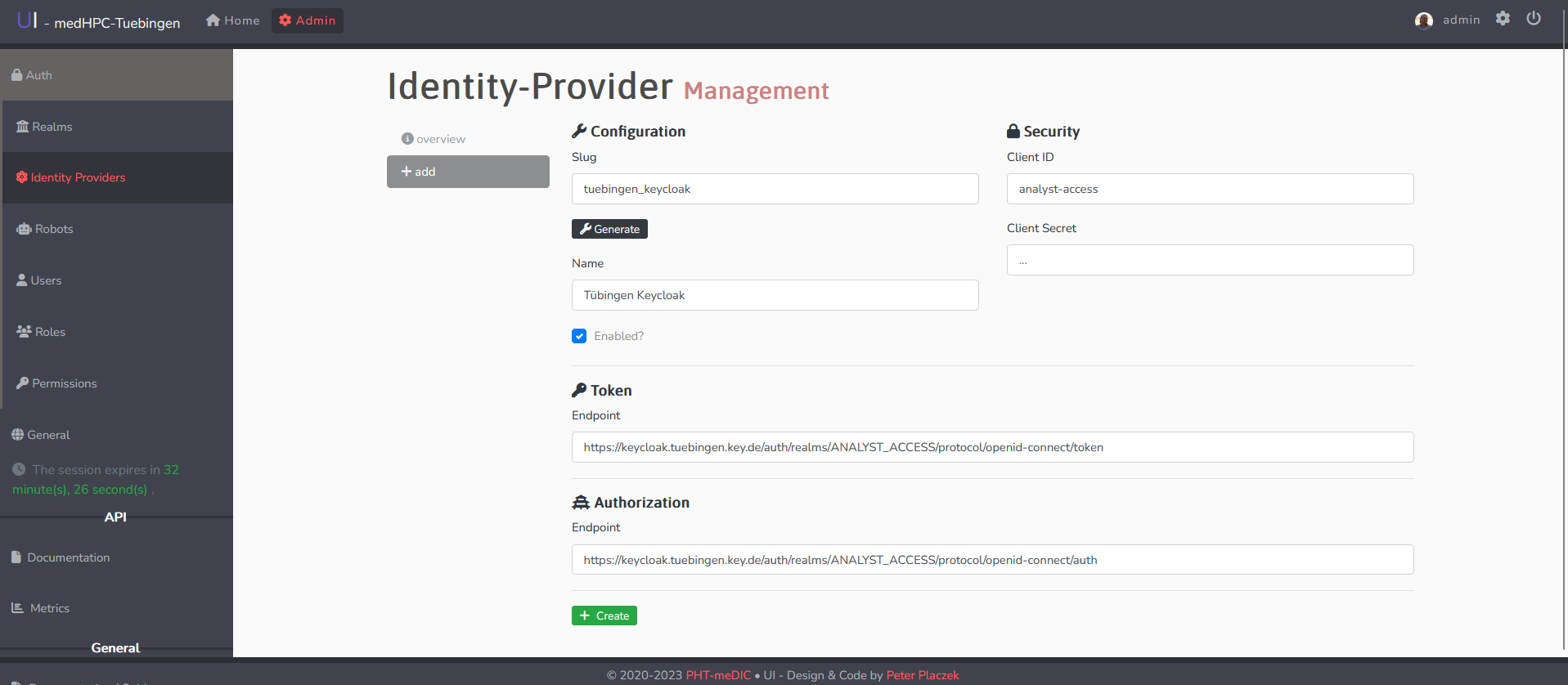
To allow each participant to control their own distribution of roles, the central UI allows the user to configure an OIDC provider which can be used to authenticate users associated with their realm. OIDC providers can be configured in the admin panel of the central UI under Auth -> Identity Providers. 
Clicking on the Add button on the left will allow you to configure a new OIDC provider. The form for adding the identity provider holds the following options:
- Configuration
- Slug: Readable slug identifier for OIDC provider configuration in the central UI. May only contain the following characters: [0-9a-z-_]+
- Name: Visible handle, shown in OIDC provider overview in the central UI
- Security
- Client ID: Identifier/Username in OIDC provider
- Client Secret: Password/Secret in OIDC provider
- Token
- Endpoint: Token endpoint for OIDC provider
- Authorization
- Endpoint: Authorization endpoint for OIDC provider
Example: Keycloak
Any OpenID-provider can be configured to be selected in the login screen to authenticate users belonging to your realm. If you don't know how to set up a client, follow the steps below for an example configuration of Keycloak.
The following settings are used in the User Interface with Keycloak as identity provider:
Slug: Unique pretty (url) identifier
Name: <Display name in UI>
Client-ID: <name of client specified in keycloak>
Client Secret: <secret of client if set to confidential>
Token
Endpoint: (e.g. https://DOMAIN.de/auth/realms/REALM_NAME/protocol/openid-connect/token)
DOMAIN and REALM_NAME need to be edited.
Authorization
Endpoint: (e.g. https://DOMAIN.de/auth/realms/REALM_NAME/protocol/openid-connect/auth)
DOMAIN and REALM_NAME need to be edited.
Create a Realm in Keycloak
- Create a realm - in this example:
PHT_DEV - Create a new client within this realm - in this example:
pht-staging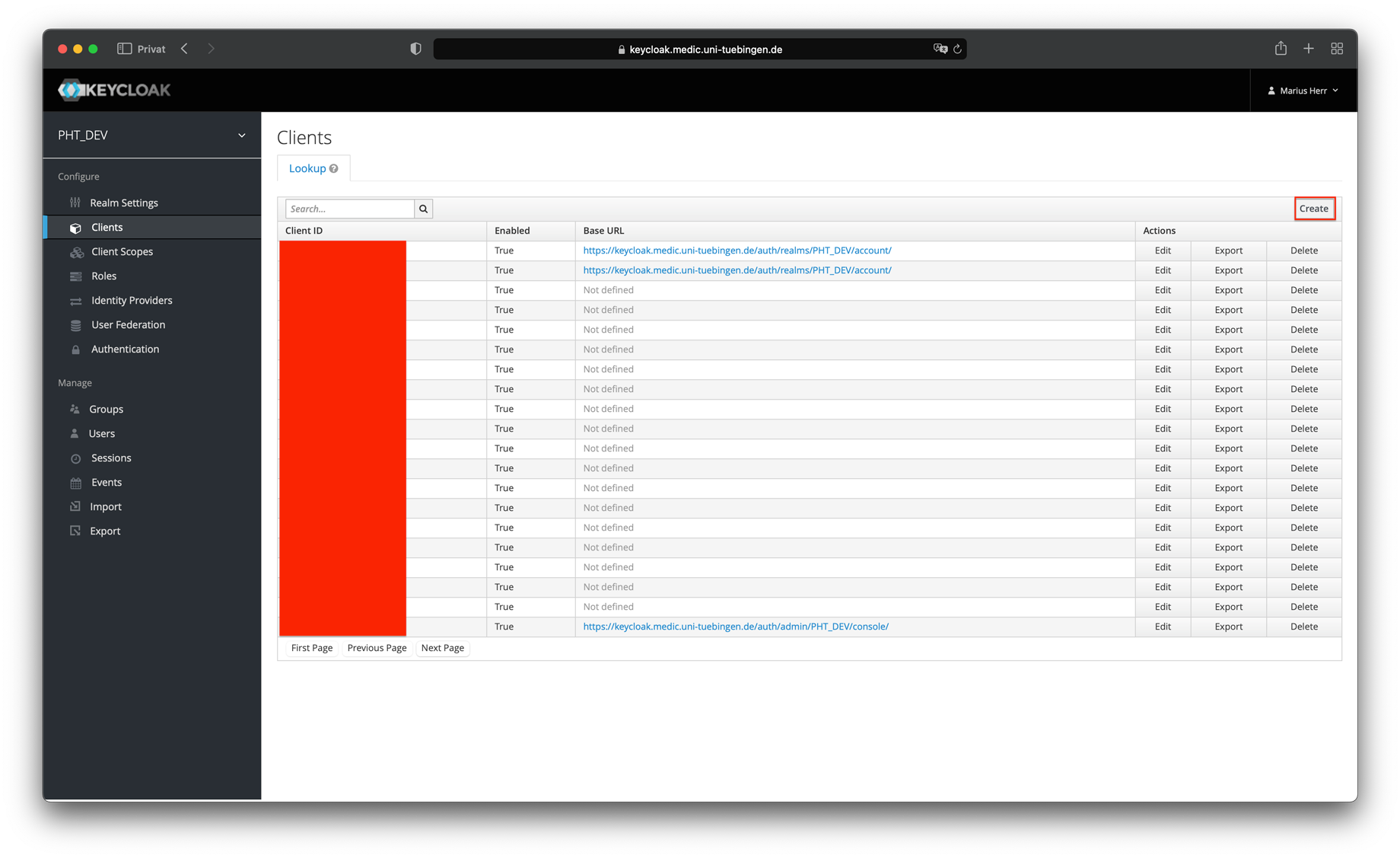
- Set the access type to confidential and a root URL and the valid redirect URIs
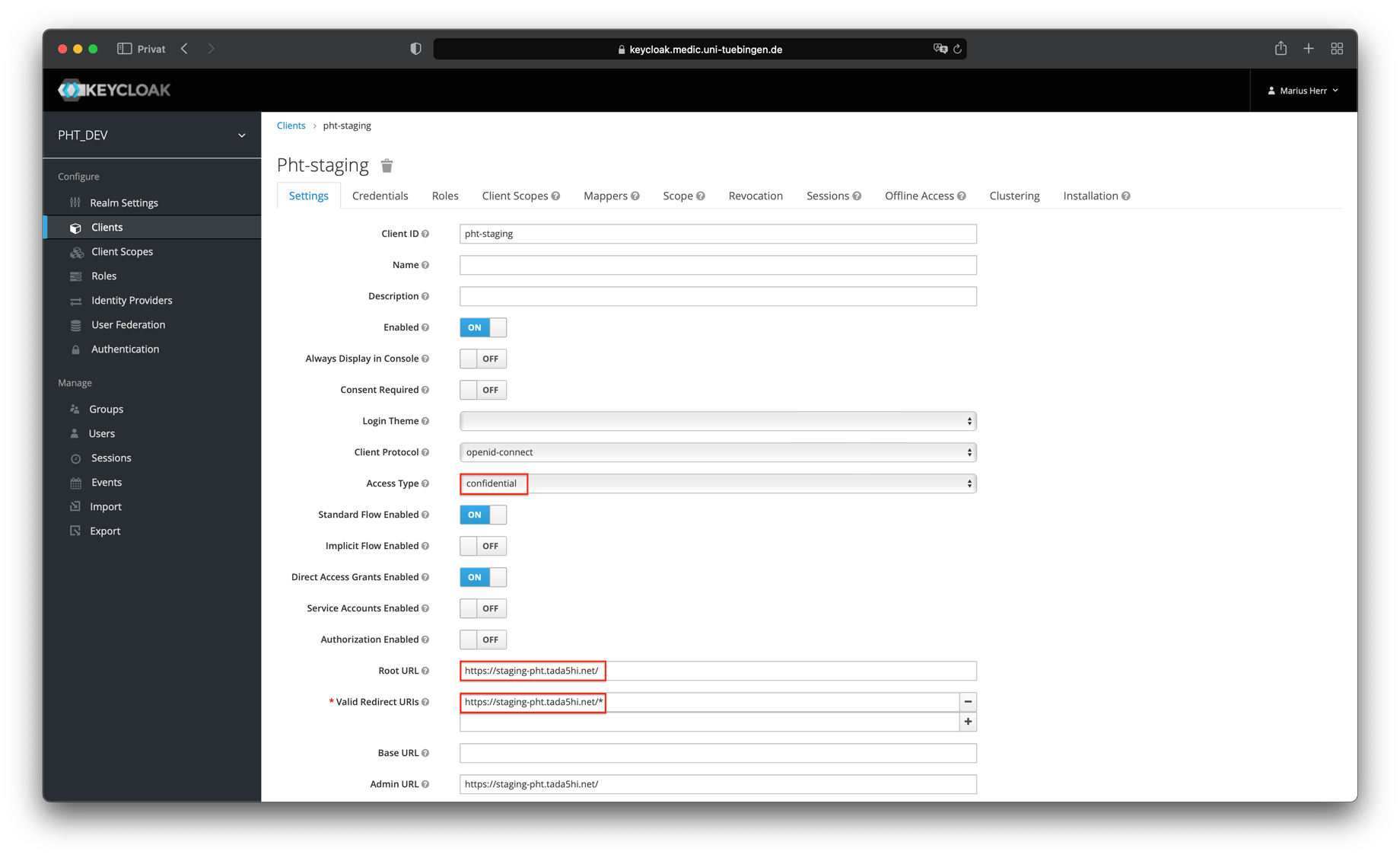
- Copy your client secret and use it for the configuration in the UI
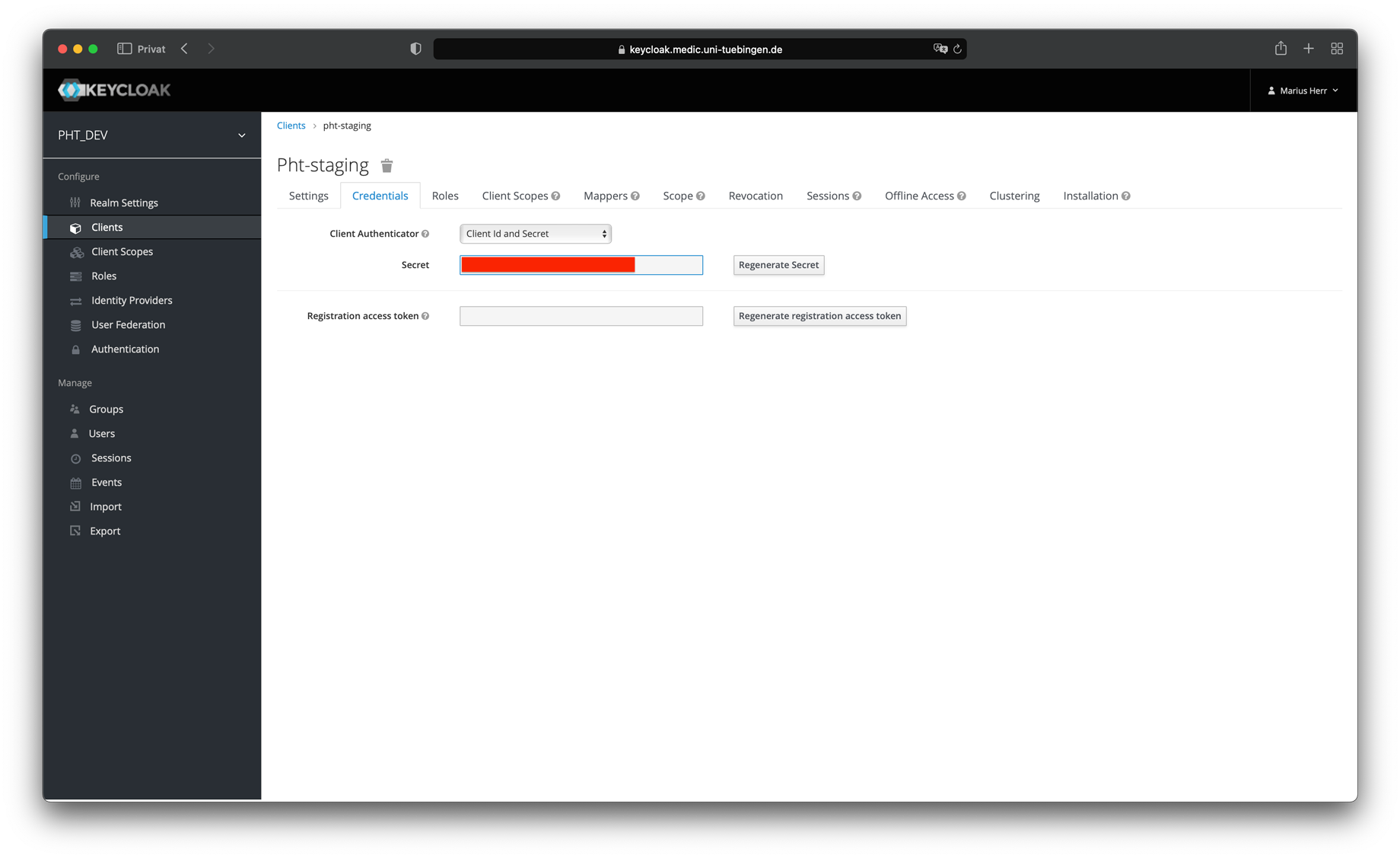
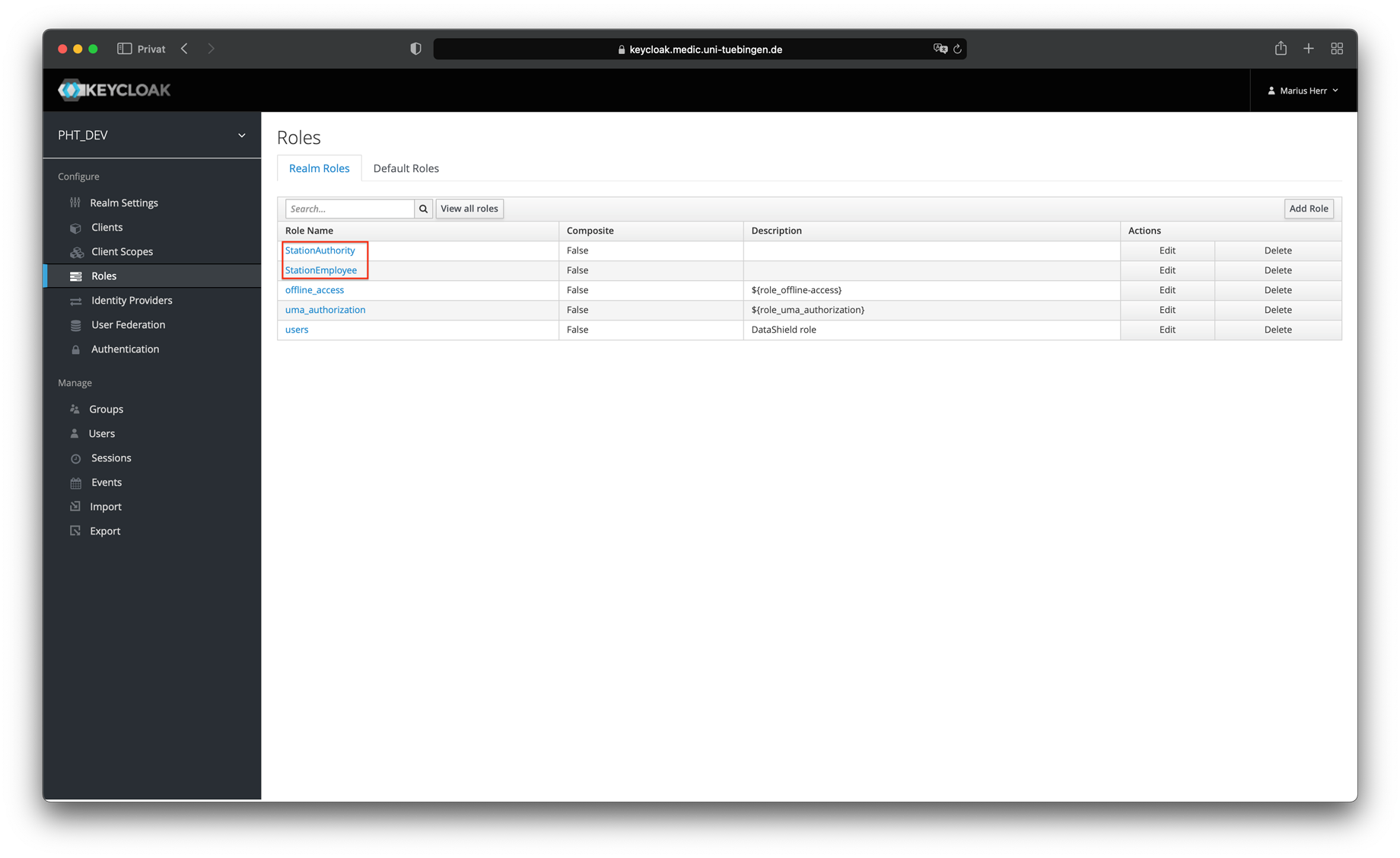
- The following two roles must be created in the identity provider
Management
- Within the admin area (top left), you need to select Identity Providers within the left navigation.
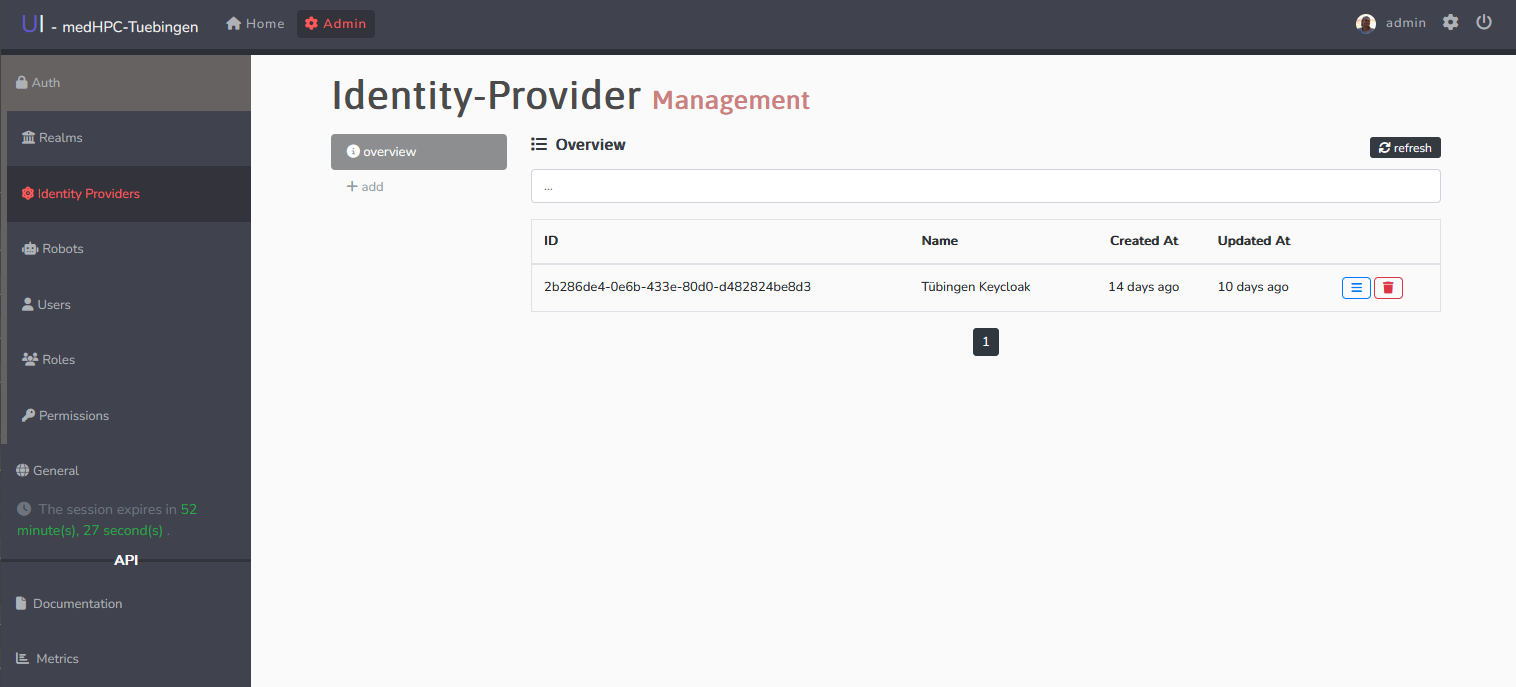
- View existing identity providers (Optional: Use the search bar at the top).
- See/Edit details and roles for each identity provider by clicking the blue triple-bar button on the right. Doing so shows the general description of the identity provider configuration.
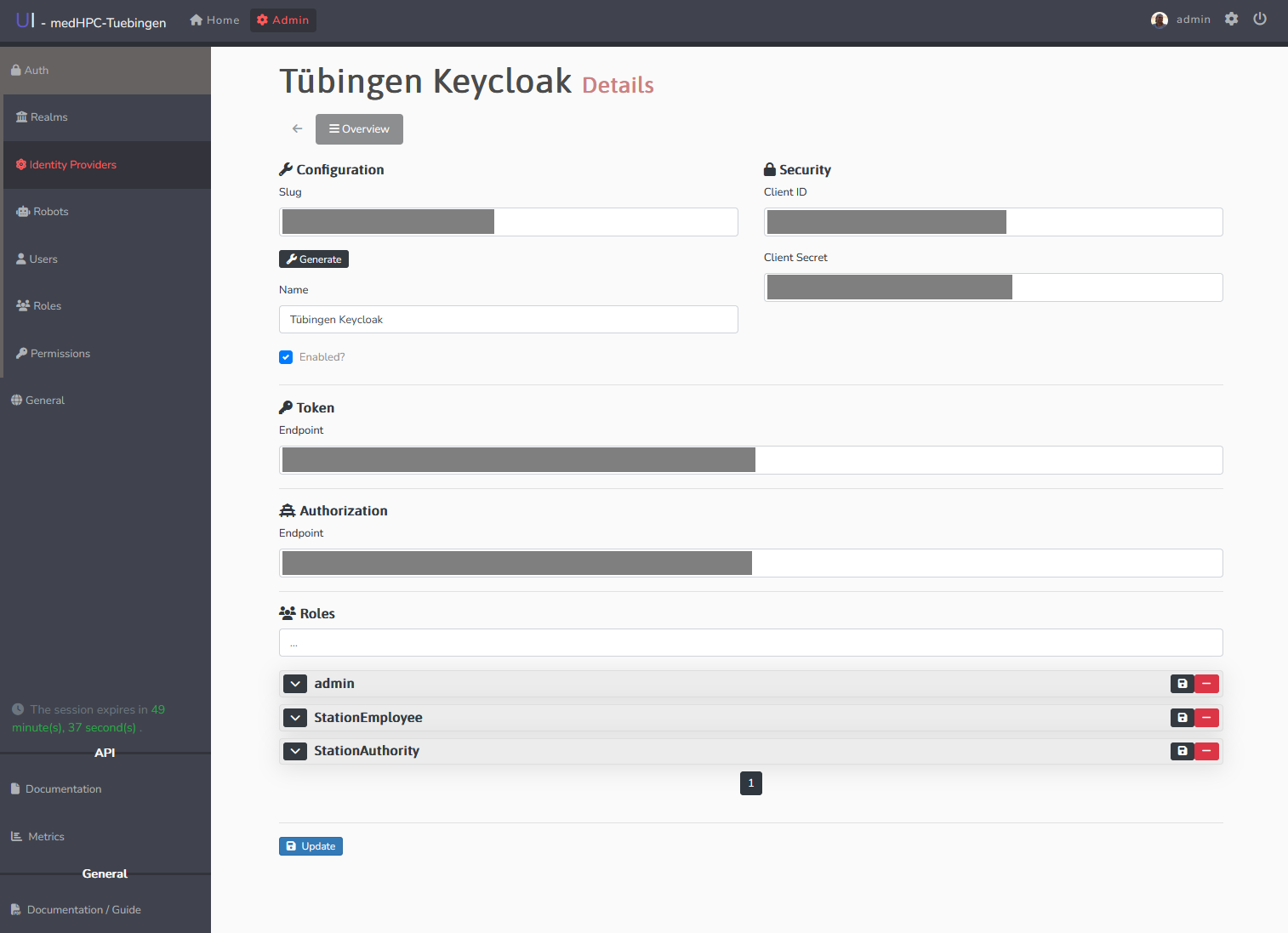
Here you may also change roles automatically assigned to users, that use this identity provider at the bottom, by either adding a role with the green plus-button, or deleting it with the red trashcan-button. Individual changes here have to be saved by clicking the respective black save-button. - Delete identity providers by clicking the red thrash can button on the right.
- Add identity providers by clicking the grey plus button on the left of the overview (for details see description at the top).
- Refresh this list anytime by clicking the black refresh button on the top right.